After a botched solar panel install from a shady contractor at my parents’ place, they left behind some random stuff after finishing up and one of those things was a WiFi data logging stick for the inverter. The box itself had no name attached to it and I didn’t think to ask what brand the inverter was before way later, hence the bad end.

Normally i wouldn’t care much for any of these things but for some reason this thing called out to me and wanted me to open it up and have a look inside – at least that’s what my nightmares told me.
After prying it open and having a quick look at the circuitry, I saw its inputs had a voltage regulator attached to it that could handle up to 24V – so the first thing was to solder a few wires to the positive and negative terminals and boot it up.
Nothing fancy happens upon boot, just a red LED that turns on – however i did notice that the board had 4 in-line copper-laden holes on it with no markings. Could this perhaps be an exposed UART ready to be tampered with?

Oh gosh it certainly is! After probing a bit with my oscilloscope i found the rx/tx pins, hooked it up to my serial connector board and booted up a terminal on my computer.
At first glance, nothing of real interest is showing up except for the “press W for cli” menu thing. Could it be an entirely open cli/shell left open to poke around in? Could the vendor really have overlooked this?
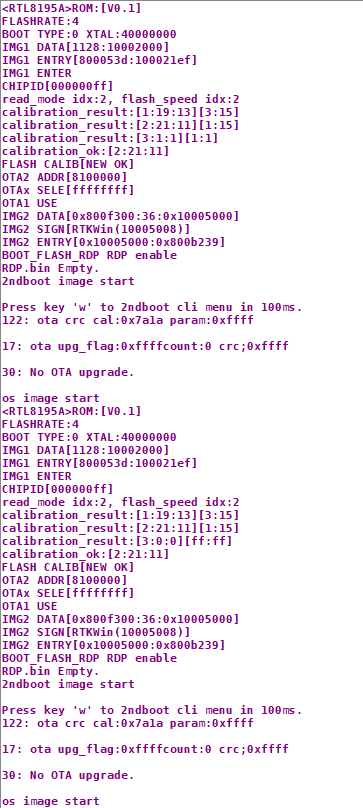
After setting up my terminal to respond with a w upon encountering that specific string, I got access to the command interface – success!
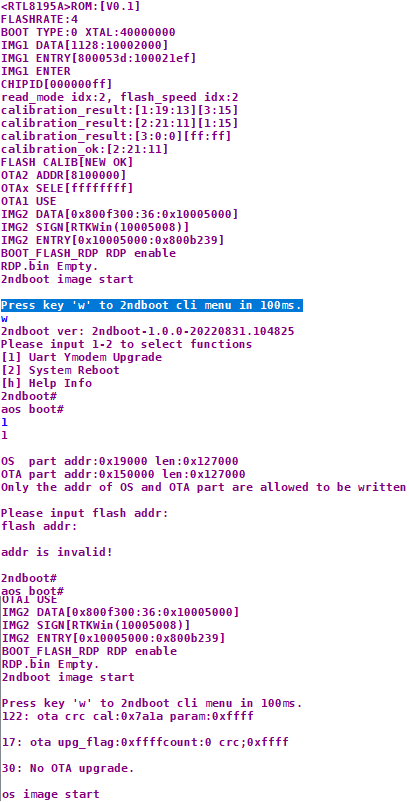
Albeit a very lackluster success! The shell is completely closed off from anything fun or interesting, unfortunately. After looking around on the board a bit more i decided to check out the chip itself in more detail. After searching up the EMW3080-E I came across the datasheet and immediately went looking for anything that contained the words “program” or “boot”, hopefully leading me to something that would let me access the bootloader or an elevated shell.
And bingo, there was indeed merely a matter of pulling pin 21 low to access the bootloader config – so I soldered a wire and a 100k resistor to the pin and booted up again.

Now this is where the fun and disappointment begins! After finally opening up the bootloader i wasn’t entirely sure how to extract/dump the contents, so I went searching – only to find that I wasn’t the first person to try this. In fact someone has already completely reverse engineered it AND the protocol for use in home automation systems.
While it was fun to poke around and finally extract the data, I had no desire nor reason to continue this specific endeavor unfortunately.